Chapter 2: Network Layer Attacks and Defense
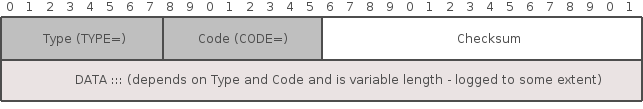
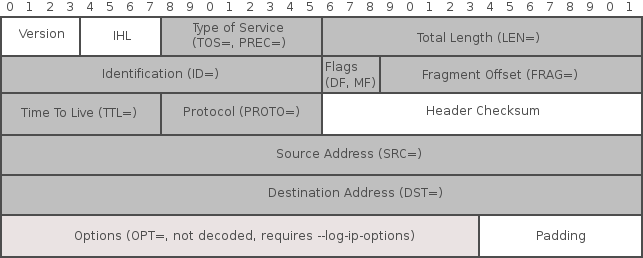
This chapter shows the types of attacks that exist in the network layer and what you can do about them. I'll introduce you to the iptables logging format and emphasize the network layer information that you can glean from iptables logs.The following figures that represent the completeness of the iptables logging format for IPv4 and ICMP headers are discussed in Chapter 2.
iptables LOG Coverage of the IPv4 Header:
iptables LOG Coverage of the ICMP Header: